Cyber Attack
Simulation
Proactively Identifying Security Vulnerabilities through Cyberattack Simulation
In an era marked by escalating cyber threats, ensuring comprehensive protection has become a paramount concern for professionals. With cyber attacks growing in complexity and audacity, they pose not only financial risks but also the potential for malicious code creation and even political activism. The repercussions of cyber attacks are vast, with intruders having the power to exploit systems or stolen data for their purposes.
To fortify an organization's defenses, it is imperative to comprehend security vulnerabilities from a hacker's perspective. This understanding is pivotal in gauging the real threats faced by an organization and in bolstering defenses against increasingly sophisticated cyber attacks. This is where Edibbee comes into play. Through cyber attack simulation exercises, Edibbee has the capacity to uncover both known and previously undiscovered vulnerabilities by subjecting systems to real-world threats.
Edibbee employs a set of customized, rigorously tested, and proven methodologies to assess weaknesses in physical security, personnel, procedural security, as well as system and application-level security.
Steps For Conducting Cyber Exercise
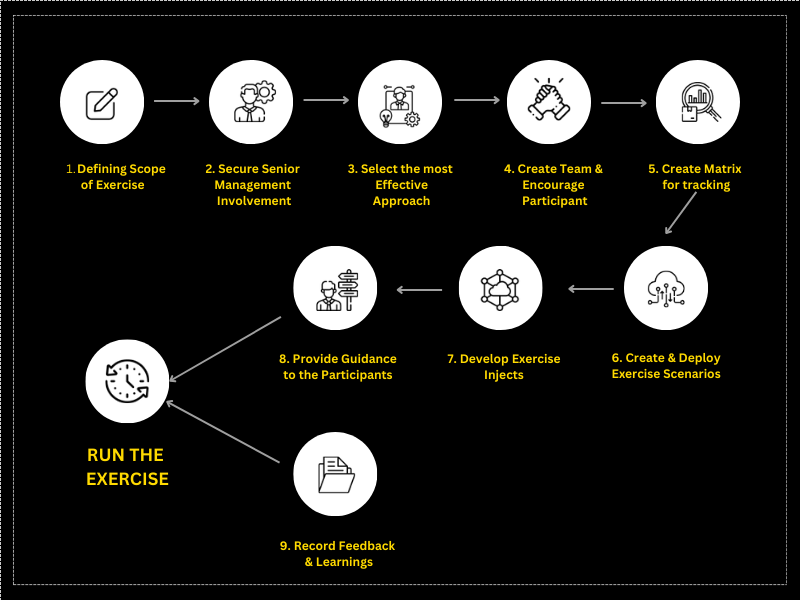
What is cyberattack simulation?
Cyberattack simulation software is a tool employed to replicate real-world security threats with the aim of uncovering vulnerabilities within a business's security infrastructure and formulating incident response strategies. These simulations may involve sending fictitious phishing attempts to employees or launching attacks on the organization's web application firewall. They frequently incorporate automated simulations, harnessing AI-driven threat logic to ensure that the security team remains vigilant at all times.
The simulations are highly adaptable and tailored to meet the specific needs of each client. They are available for use around the clock but can also be utilized periodically, as dictated by the client's requirements. Regardless of whether a manual or automated approach is adopted, accurately assessing the effectiveness of security operations can be a daunting task. Our customized software is designed to simulate a wide range of threats across diverse environments, enabling our clients to effectively prepare for and evaluate their security posture.
The cyberattack simulation exercises encompass various attack vectors such as phishing, malware assembly and binding, SQL injection, distributed denial of service (DDOS) attacks, and other exploits. These exercises offer deeper insights to the Chief Information Security Officer (CISO), Chief Financial Officer (CFO), and Chief Executive Officer (CEO), empowering them to enhance the organization's security defenses.
What is cyberattack simulation?
Our approach involves thinking like malicious threat actors in order to discern exploitable opportunities. We utilize publicly available information to gain insights from a hacker's vantage point, going beyond the confines of conventional penetration testing. This strategy allows us to appreciate the strategic significance of tactics, assets, geographical factors, and other considerations that matter to hackers. By doing so, we simplify the process of pinpointing security weaknesses within an organization's defense mechanisms, particularly when safeguarding its most prized assets.
How about understanding your threat position? Let's arrange a confidential cyberattack simulation now.
Why Cyberattack simulations?

Realistic Assessment
Uncover Unnoticed Vulnerabilities and Weaknesses Not Evident via Conventional Security Methods.

Improved Incident Response
Assess and Improve Incident Response Proficiency, Gaining Valuable Insights into Threat Management Effectiveness.

Proactive Risk Management
Take Preemptive Action to Discover and Mitigate Security Weaknesses Prior to Exploitation by Actual Threat Actors.

Enhanced Security Awareness
Promote Employee Awareness Regarding Diverse Cyber Threats and Attack Strategies.

Compliance Adherence
Cyberattack simulations aid in verifying that security measures adhere to industry regulations and standards.
Clientele











Have an idea in Mind? Speak to us today.
A strategy session is perfect for:
- Autonomous Simulations of Cyberattacks, Mimicking Genuine Hacker Tactics.
- Focused and Actionable Remediation Recommendations.
- Raising Security Awareness Among Personnel.
- Consistent Updates on Evolving Threats.
- Assessing Ongoing Risks and Implementing Mitigation Strategies to Safeguard the Organization.
Frequently Asked Questions
Cyberattack simulations offer a realistic evaluation of an organization's security stance. These simulations replicate actual attack scenarios, making it straightforward to identify vulnerabilities and weaknesses that might elude traditional security measures. They play a proactive role in strengthening security defenses, enhancing incident response capabilities, and mitigating potential risks.
Cyber Attack Simulation encompasses a broader assessment, replicating real-world attack scenarios that encompass various elements such as social engineering, physical security breaches, and multi-stage attacks. It aims to evaluate the overall security posture of the organization.
On the other hand, Penetration Testing is more narrowly focused. It concentrates on the identification and exploitation of specific vulnerabilities to gain unauthorized access, centering its efforts on individual systems, applications, or networks.
We provide a diverse array of security assessment services designed to fortify an organization's defenses. Our offerings encompass simulated phishing campaigns, social engineering evaluations, physical security assessments, network penetration testing, application security testing, and comprehensive red teaming exercises.
The frequency of cyber attack simulations is contingent on several factors, including the organization's industry, risk exposure, regulatory obligations, and the ever-changing threat environment. While a minimum annual cycle is advised, entities with elevated security risks or rigorous compliance mandates may opt for quarterly or semi-annual assessments to maintain a consistently robust security posture.
Edibbee's expert team orchestrates controlled cyberattacks on your organization, intending to penetrate the infrastructure, assume control over specified targets, and securely extract them. This process reveals the potential impact of vulnerabilities spanning from technology to employee awareness on your business.
Absolutely, our cyber attack simulation services can be tailored to cater to your distinct business requirements. We acknowledge that each organization possesses unique security demands influenced by their industry, regulatory mandates, and risk tolerance. As a result, we provide personalized solutions to align with your organization's precise security objectives and needs.
? In a cyber attack simulation, an organization (and its security partners) emulates an actual hack against its own network, infrastructure and assets using the tools, tactics and procedures (TTPs) of known cyber criminals.
Breach and attack simulations are an advanced computer security testing method. These simulations identify vulnerabilities in security environments by mimicking the likely attack paths and techniques used by malicious actors.



